

The Company
Secure-IC is a spin-off from Télécom ParisTech University, one of the most advanced institutes in embedded security research. Sylvain Guilley, Jean-Luc Danger and Laurent Sauvage, Paris Tech researchers and inventors of more than 50 families of patents on embedded security have founded Secure-IC jointly with Hassan Triqui and Philippe Nguyen in January 2010.
Mission and Values
Secure-IC mission is to partner with our clients throughout and beyond the IC design process to provide best-of-breed security expertise, solutions, and technologies, for embedded systems and connected objects. More than
just words, our values define how we conduct ourselves and our business on a day-to-day basis. Our values are vital to the success of Secure-IC and the trust of our clients.
We are pioneers
We are committed to being a good corporate citizen
We are a people company
We are proactive
And above all, we exceed client expectations
Governance
Corporate governance is an integral part of the Secure-IC corporate culture and it is founded on our values. We are committed to high standards of corporate governance, as we consider this contributes to the company’s long-term success. Our commitment to efficient company management is how we gain and keep the trust of employees, customers, partners, and communities in which we work and do business.
The Strategic Board:
Jean-Charles Hourcade, Chairman
Hassan Triqui
Philippe Nguyen
Sylvain Guilley
Jean-Luc Danger
Laurent Sauvage
David Naccache, Chairman of the Scientific Committee

Mobility has now come into payment. While magnetic stripe is bound to extinction and mobile devices are coming closer to customers’ banking account, a mandatory condition for new payment devices to be adopted is the confidence of users in the security of their transactions.
Standards and norms (such as PCI and EMV) are developed to set high security standards and guarantee an overall level of confidence.
Secure-IC has worked with big players in the banking and payment field and is able to provide both advices and technologies to be compliant with the highest and most widespread standards.

Electronic passports have allowed travelling over the world with great simplicity. By deploying complex cryptographic systems called PKI (Public Key Infrastructures), it is now possible to design identity documents impossible to counterfeit? However, the data contained in identity documents have to be both non-clonable and unreadable by unauthorized entity, during all the lifecycle of the documents, while maintaining a seamless mobility. Such requirements were described by the International Civil Aviation Organization (ICAO) to establish a reference for biometric passports. Secure-IC is an ideal partner to understand those requirements and match them by providing appropriate and customized technologies.

Connected objects are about to invade our daily lives: smart watch, smart home, smart city … will be the source of mass hacking. But with all devices connected, each one is becoming a single point of failure for the whole network. Therefore, the amount of money at stake in case of security hacks of connected devices exceeds by far their commercial value. However, mass hackings, with growing impacts, are regularly reported in the news (e.g. http://www.nytimes.com/2016/10/22/business/internet-problems-attack.html) .

As a founding member of the IoT Security Foundation (https://iotsecurityfoundation.org/), Secure-IC has been involved for several years in raising the security level in IoT & Cloud while taking into account the constrained resources of lightweight devices. Check our Protect offer to discover our toolbox of security technologies.

Security and trust in the Media need to be reloaded. Millions of dollars of revenue are lost every year by Studios because piracy and premium content theft. With the emergence of enhanced premium content such as 4K Ultra HD and HDR (high dynamic Range), Hollywood studios requires new security measures derived from cryptographic solutions: Premium content protection is now at every
point in the consumption lifecycle.
Thanks to the core expertise and experience of its founders involved for several years in Media & Entertainment activities, Secure-IC, a member of the UHD Forum, enhances content protection by
offering an innovative end to end solution in respect with the last Movie labs recommendations.
Public actors’ concern for cybersecurity has been constantly growing for the last decades. Because they meet security issues arising from various application fields (identity, evaluation, defense) and require extended lifecycle solutions, public actors have high expectancies in security, certification expertise and technologies’ level. For them, Secure-IC has thought out offers of long term collaboration containing advanced trainings, above state-of-the-art technologies and consulting sessions.

The Trusted Computing Group established in 2009 the standard ISO/IEC 11889 specifying a secure module for secret storage. It combines software and hardware technologies in order to bring computer assets features such as platform integrity, disk encryption, password protection, digital right management, protection of software licenses… As specifications and security requirements evolve, each TPM implementation is a challenge that Secure-IC has successfully taken up by providing its security technologies to TPM manufacturers who managed to pass FIPS and CC certification (EAL 5+). Check our Securyzr offer for more information.

Autonomous cars are the future of automotive. Today, connected cars have already tremendously changed our ways of driving and usages of cars. After years of improvements of cars’ safety, the time has come for a rise in cars’ connectivity to bring additional safety, comfort and ergonomy in the vehicles. Communication networks of different kinds are under deployment, for communication between one vehicle’s modules, between vehicles(V2V, Vehicle-to-Vehicle) and from one vehicle to a central server (V2I, Vehicle-to-Infrastructure). They require the use ECUs (Electronic Computer Units) with different constraints in resources and security. But for each of them, a security breach can end up in an industrial failure.
To avoid those, Secure-IC provides its partners with its expertise and knowledge of the current initiatives defining a framework for automotive security on a large scale (e.g. (EVITA, PRESERVE projects),
and provides the appropriate security technologies.

Security evaluation centers, whether public or private, are a necessary condition to guarantee users’ trust in electronic devices and ensure digital markets’ growth. However, evaluating electronic devices security is a time-consuming and highly technical task. Attacks are permanently evolving, and the amount of connected devices to be evaluated has skyrocketed. For evaluations laboratories, smooth and reliable evaluations are a key success factor. For designers, detecting weakness before deployment and/or certification phase is crucial to accelerate time-to-market. For all of them,
Secure-IC has developed the appropriate tools.
Secure-IC proposes to its clients and partners a full range of products and services. Our Protect offer contains a complete set of hardware and software technologies to include into your design in order to make them attack-resilient. The Evaluate offer is a product line dedicated to the security assessment tools. Our Service offer completes these products to provide the necessary help and knowledge for an optimal use.
Securyzr
On October 20th, 2016, many of the most commonly visited websites in the world, such as Facebook, Twitter, … were unreachable for several hours. Had the targeted infrastructures been different (airports ? public transportation networks ? financial institutions ?), devastating consequences would have been to deplore. This breach was made possible by hacking simultaneously 10 millions of poorly protected connected devices.
Thus, with the coming advent of connected objects, cars, cities, etc …, the need for security technologies efficient and easy to deploy is about to rise dramatically.The aim of Secure-IC Securyzr is to address all the state-of-the-art threats with a single product. Condensing our advanced technologies, this multi-usage easy-to-integrate solution is the Future of Security.
Secure-IC Securyzr provides the core security services required to build a security architecture for a wide variety of devices : mobile, connected object, payment device, smart card, ECU, Set-Top-Box, HSM, etc.
Key features
Customizable API
Fully digital tamper detection
Possibility to use external CPU
Certification ready
Wide range of configurations to adress each market constraints
Lightweight and low-power for IoT, Mobile
High-bandwith for Automotive
Content protection technologies included (API and accelerators) for Media & Entertainment
Highest security for Banking, Identity, Trusted Computing
Security functions
Root-of-trust: Secure Boot and Secure Secret Storage (unique ID, secret key)
Security Monitoring: Secure Debug, Lifecycle Management API
Hardware acceleration for high performance cryptographic computation
Software libraries for public-key signatures, symmetric cipher suites, and hash engines
Strong tamper resistance: fault injection and perturbation attacks resilience
Contact us for more information.
Smart Units have been designed to answer customers’s common needs. These sub-systems are ready and easy-to-use solutions that can be customized to match specific requirements.
Boot Protection Pack
How to guarantee that the system will boot in a secure environment?
This pack provides a secure root-of-trust with a high level of resistance against malevolent attacks. It ensures integrity of the SoC security features and guarantees that the firmware is genuine.
Optionally, it ensures the firmware’s confidentiality.
The Boot Protection Pack is designed to thwart the following threats: fault injection, side-channel analysis, invasive probing, invasive modifications, software vulnerabilities exploitation. All the
verifications are performed in a hardened boot sequence which cannot be circumvented.
Key Protection Pack
Hiding a cryptographic key in electronic devices is necessary to guarantee fundamental security features, such as device authentication or firmware encryption. Secure-IC Key Protection Pack is a highly secure key storage solution relying on our PUF-based Strong Secret Storage technology and resilient Key Wrap (Tunable Crypto Key Technology).
Data Protection Pack
Storing data securely in a non-volatile memory requires not only encryption of data-at-rest, but also secure access to the memory, protection of data-in-transit … To guarantee fast and full protection of stored data, Secure-IC has combined its resilient cryptographic technologies (AES or other cipher-based), bus protection, efficient DMA. Customizable according to performance/security/space requirements, it will fit any design.
Authentication Pack
How to establish a secure link between two entities that need to exchange sensitive data?
A mandatory step is to be sure that the interlocutor to talk to is the good one.
This pack includes all the necessary secure elements (cryptographic modules embedding countermeasures, random number generator, secure Test Access Port, etc. to achieve the authentication of the user to communicate with.
Content Protection Pack
How to extend the security of your asset when your contents are on the clear?
Secure-IC Content Protection Pack provides technologies to detect, track and identifies pirates and enforce your rights. The Pack is available for integration on ASIC and FPGA (Hardware IP) and server (Software lib). It provides Digital Cinema class quality for 4K HDR solution, robust to camcording and low bitrate attacks.
Does physical security evaluation restricted to experts? No more, Laboryzr provides a ready-to-use Evaluation laboratory including engineer training.
Secure-IC recommends as security expert to gather Design For Security (DFS) approach with Evaluation all along the product life cycle.
Laboryzr allows security evaluation at both at pre-silicon stage and at post-silicon stage. Such evaluation all along the product life cycle is at least unique. Laboryzr does more, it provides also Catalyzr to speed-up evaluation and make evaluation results easy to interpret.
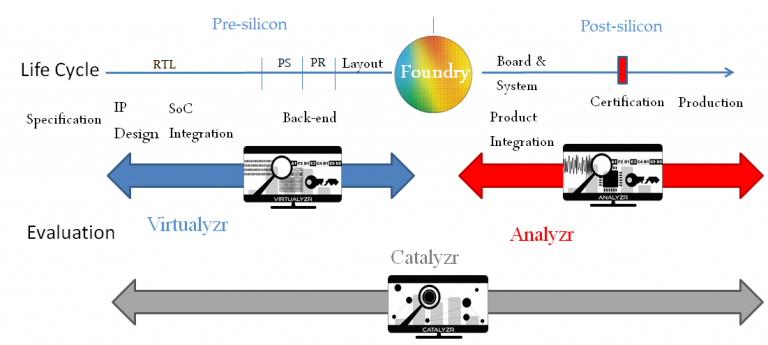
Laboryzr includes 3 tools and Lab’s equipments:
-Virtualyzr tool is the only one tool which allows to evaluate side-channel security during this pre-silicon design stage, from the first source code of IP (Intellectual Property) toward SoC Layout (GDS2) just before going to foundry.
-Analyzr tool does physical security evaluation on real physical chip/board from foundry. It includes all material platforms to perform SCA measurements and FIA injection, then analysis.
-Catalyzr tool emphases Virtualyzr and Analyzr performances. It optimizes acquisition step by detecting leakages and advises tools where to look. And after analysis, Catalyzr pre-interprets results and gives tips as an embedded evaluation expert.
Laboryzr does more again, it deliver a ready-to-use evaluation laboratory with all needed tools and also provides an in-depth engineer training.
Laboryzr gives you the Lab, knowledge and skills on the-shelf!
Analyzr is the ultimate in-lab tool for attacking and analyzing the security design of any embedded system; it was developed by security designers, for security designers and certification labs. The user interface is highly-advanced and yet extremely user-friendly. In addition to licensing the platform software, Secure-IC also provides tools to perform active attacks. Plug in your algorithms, attack, analyze at the bit level, reinforce.

Our scientists have authored some of the most advanced and highly regarded side-channel analysis and protection methodologies.
Advanced modules
Preprocessing
6D-Cartography
NICV Analysis
Fault Exploitation (DFA)
Report Generation
ISO-17825 standard
Key Features
State-of-the art attacks
Single integrated tool for Side-Channel Analysis and Fault Injection Attacks
Classic & advanced techniques
Analyze standard or self –authored algorithms
Unique ability to analyze leakage at the bit level, and precisely measure security-level
Real-time acquisition, analysis and processing
Intuitive graphical interface
Standard packages for beginner or expert users
Customizable packages
One-button, analysis reports automatically generated
FIPs-140 and ISO-17825 ready
We sum up the basic workflow of Analyzr below.
Step 1
Real Target
Step 2
Real acquisitions
Step 3
Security Analysis & Report
The Virtualyzr is a pre-silicon security evaluation platform. Assessing your cryptographic design at an early stage allows you saving a lot of effort, time and money.
The Virtualyzr takes your design as input and returns an evaluation report about the real security resistance against physical attacks.
Both classes of attacks are considered: Passive analyses like Side-channel attacks (SCA) and active analyses like Fault attacks (FIA). The platform allows the detection, localization and analysis of the security leakage in the design at all levels of conception: RTL, Post Synthesis and Place & Route levels. Indeed, several errors of miss-integration , weak countermeasure or bad optimisations could be behind the security leakage.
More importantly, with the Virtualyzr you are evaluating the power of the best ever attacker. Actually, the evaluation is performed in the best conditions based on noise-free models and full access to the design signals.
Two types of analysis are possible :
Black box-based analysis assumes that the secret is unknown and tries to recover the secret information. This allows measuring the extent of an attacker: how much time he needs to break the system. The Virtualyzr provides the last and powerful analyses existing for SCA and FIA.
White box-based analysis assumes that the secret is known and tries to focus on how such secret is behaving. In this context, the Smart-SIC Virtualyzr provides powerful metrics based on advanced statistical computation derived from the recent literature of physical analysis.
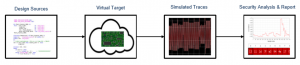
The high-level description of the internal process consists in three steps, detailed below.|
Step 1
The design is simulated according to its level conception (RTL / Post Synthesis / Place & Route). Simulated traces are obtained. The Virtualyzr allows the user to select and probe the nodes to be tested.
Step 2
The simulated traces are investigated and processed based on a mathematical consumption model to generate the so-called leakage traces. These traces are an image of the security leakage that can be exploited by an attacker to retrieve a sensitive information like a secret key.
Step 3
An advanced physical analysis is performed on obtained leakage traces. Two types of analysis can be performed: black-box or white-box analysis.
Catalyzr brings the Big Data and Machine Learning Techniques into Embedded Security to accelerate and simplify the Evaluation.
Catalyzr is an All-In-One tool to manage the datasets, locate the leakage and extract information:
From the evaluated system
From the Side-Channel measurements
From the analysis results
Designed as a Data Mining environment, it helps the user extracting the critical information before and after the Side-Channel analysis.
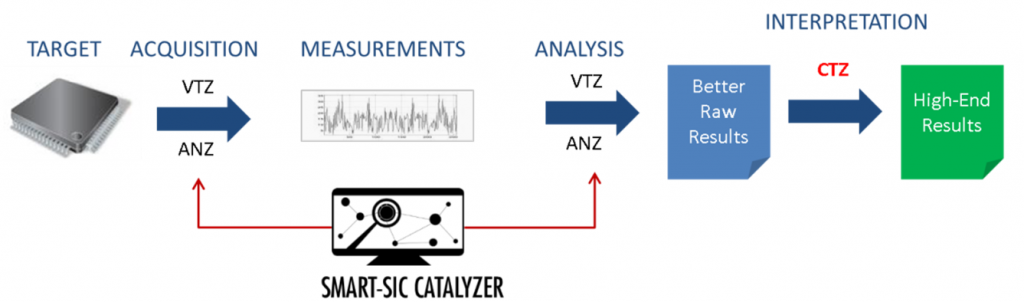
BEFORE THE ANALYSIS
Before the analysis, it can be very difficult to know where the leakages are in the large campaigns of measurements acquired on the target.
Catalyzr guides the analyst toward the leakage thanks to its high-end Leakage Localization modules.
The software can be seen as an exploration drone in the multiple dimensions of the datasets. In a few steps, it is possible to browse, filter and edit your measurements campaigns.
Catalyzr provides a library of advanced processing to Scan and Transform your waveforms: Time/Frequency, Pattern Matching, Machine Learning, Classification, Leakage Metrics. These processing cross the sources of information to reveal points of interest and sort the waveforms.
The tool will output the potential attack paths and location of leakages in the measurements, as well as the reduced datasets with only the relevant parts.
These outputs can then be used to accelerate the classical evaluation with Virtualyzr and Analyzr.
AFTER THE ANALYSIS
After the analysis, the main difficulties are to interpret the results and to diagnose the configuration problems.
Catlyzr applies the Big Data techniques to the results of the evaluation to provide a better understanding of the results and find the best parameters. It will output high-end results and the optimal parameters for analysis and preprocessing. The user can have a full profiling of the evaluation and correct quickly the configuration of tools such as Virtualyzr and Analyzr.
COMPLEMENTARY AND FULLY CUSTOMIZABLE
Catalyzr is highly complementary to other evaluation tools. The Conversion Wizard feature allows integrating any proprietary format as input and output of the platform. In a few steps the user specifies the structure of his format. He can then validate the conversion on a few samples. Finally, the new format is added to the available input and output of Catalyzr.
The processing library can also be extended with Custom Processing feature to support new localization methods. The user only needs to follow the plugin creation procedure.
To help our clients benefit from our products, Secure-IC experts accompany them through various kinds of services.
At the early stage of a project, Secure-IC offers trainings on Security Certification and good practices to build a secure architecture.
During the specification stage, we accompany our clients in the definition of their technological needs according to the desired security level and in the construction of a security architecture fitting them.
During our clients SoC design phase, Secure-IC can also achieve system level review to highlight potential weaknesses in implementation and propose guidance and countermeasures to enhance the security.
To accelerate integration, we make all of our clients benefit from our expertise in the deployment of our technologies. Support can be brought remotely but we are also capable to send our engineers at our customers’ premises.
To avoid extra costs and delayed time to market, validate your design prior to the certification process, Thanks to our home-made Evaluation tools, Secure-IC can provide on-chip characterization of the level of resistance against attacks of our products after integration in clients’ designs.
Secure-IC supports its clients during the certification process by providing help to answer laboratories’ questionsand providing the evaluation laboratories with all the required details on its technologies. Thanks to its analysis tools (Virtualyzr and Analyzr), Secure-IC can also deliver security robustness pre-evaluation reports.
Because threats are constantly evolving, Secure-IC keeps long-term relations with all its clients to maintain the highest level of threat protection and awareness.
Based on several years of research, Secure-IC fine-tuned world-class protection and evaluation technologies allowing its customers to master the threats against their embedded systems. They can be easily deployed in your systems, or you can benefit from them through Secure-IC ready-to-plug solutions (See Sections Solutions).
Attacks against digital circuits can be performed by actively disrupting the device or by directly tampering with the device’s internal structure. These powerful attacks regroup attempts to inject faults, directly probe or force signals, remove, add or modify features on the chip (metal routing, transistors).
Against such attacks, Secure-IC offers a range of protection technologies including shielding, tampering detection, digital attach sensing, and data at-rest/in-transit scrambling.
Key Features
Digital & Universal sensor, reactive to any abnormal conditions (temperature, voltage, clock frequency, laser and EM exposure, etc.)
Shielding to prevent ASIC intrusions
Alarms raised in real-time
Random jitter to desynchronize information leakage
High-performing memory encryption to protect data in real-time
Secure-IC offers a broad range of Cryptography technologies to cover customers’ needs, from Symmetric Cryptography to Asymmetric Cryptography and Hash functions.
They are designed to strike the ideal balance between the level of security you are attempting to achieve, and overhead.
Key Features
Fine-tune level of security/cost
Highly-efficient processing
Above state-of-the-art security
Storing a secret in an electronic device implies leaving physical marks of the data stored, and thus is prone to direct reading or reverse-engineering. To avoid those traces, Secure-IC Strong Secret Storage technology is secret generation tool based on Physically Unclonable Functions (PUF), which exploit the random mismatches introduced during manufacturing process. As it does not modify the component, our technology ensures a real protection against the reverse-engineering techniques compared to traditional methods that store the key in a non-volatile memory or in an OTP component. Morevoer, the Strong Secret Storage Key Tech has been optimized to offer great reliability and compliance with the coming ISO standards.
Key Features
|
Also usable for challenge response protocol or ID generation
Portable into any technology
Customize Bit Error Rate / Cost
Random number generation is a keystone in security. Secure-IC offers both True Random Number Generator (TRNG) resilient to harmonic injection for statistically independent sets of bits generation and Deterministic Random Bit Generator (DRBG) for high bitrates requirements. These random generators are compliant with commonly used statistical tests suites. Key Features For crypto & initialization vectors Cannot be biased Resilient to harmonic EM injection Ultra fast, high performing
Pre-silicon evaluation is key tool to reduce time-to-market and post tape-out maintenance. By finely emulating the behavior of a device from its design, it is now possible to anticipate the security weaknesses before they become problems. As simulations consider the best attacker mode as the evaluation is conducted in perfect conditions by contrast to a real analysis usually impacted by the noise or measurement misalignment.
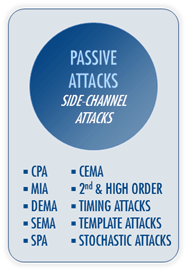
System-on-Chip security evaluation consists in assessing by precise metrics the feasibility of state-of-the-art attacks against a device. The standards ISO 17825 and ISO 20 085-1/-2, with which Secure-IC Analyzr is fully compliant, describe the most wide spread methods to perform simple and accurate evaluations. Amongst the founders of Secure-IC are contributors and editors of those standards, endowing us with a worldly renowned expertise on SoC evaluation. Fields of expertise Passive attacks (SPA, DEMA, CEMA, MIA analyses) Active attacks, Fault injection (laser, supply/voltage, over clocking, EM injection)
Hiding irremovable and invisible mark into a signal or a dataset for forensic purpose is known as “digital watermarking” or “watermarking”. This signal protection technology has been developed in the 90’s and is today quite widely and discretely deployed in many field. Security expert frequently describe digital watermarking as an extension to ciphering security when data are on the clear.
Tomorrow, the advent of a quantum computer is likely to threaten the security of our communications and data. Secure-IC is deeply involved in renewing the security technologies prior to the quantum era so as to ensure a safe and sound transition. Among our scientists, renowned experts of the field are designing cryptographic technologies resistant to quantum attacks.
In order to offer its clients best-of-breed technologies and above state-of-the-art protections, Secure-IC, The Security Science Company, is highly committed in its research community to analyze upcoming threats, explore innovative solutions, and support the work of standardization bodies. Our research activities benefit our partners through trainings or closer collaborations on specific topics.
Our scientific advisors are world widely renowned experts on embedded security and standards. Meet them to learn everything you need to know about attacks and protection of software and hardware. Trainings are adapted to any prior knowledge level and include practical sessions with our tools.
Settling a framework for security evaluation requires preparation. A starting point is to establish a road map for a rise in competences and equipments. Thanks to our trainings and our experts’ advice, you will be guided during this process so as to rationalize your choices and optimize costs and time schedule.
You have an unusual problem to tackle or above-standards evaluation to perform? Ask Secure-IC’s experts. We will provide results above expectations and detailed reports. Common research can lead to a scientific publication in major venues.
Secure-IC is highly implicated in the security research community. It has taken part in many collaborative projects on innovative topics such as cyber resistance, homomorphic encyrption, SoC hardening, laser attacks … From 2017 to 2020, Secure-IC is leading a consortium designing security products embedding post-quantum technologies.
Secure-IC is an active member of the ISO community to establish high-quality security standards. Several of its founders have acted as contributors and editors for major security standards: ISO 17825, ISO 20 085-1/-2 for criteria of security evaluations, and the under redaction standard on PUF.
With three Professors of the Mines-Telecom Institute amongst its founders, Secure-IC gathers 10 years of research and 300 publications in cyber and embedded security. Completing the research team, 10 PhD students contribute to the scientific excellence of Secure-IC on both current and future technologies.
Going forward, there will be more and more interconnected devices or objects in various market verticals, this is what we call Internet of Things or Internet of Everything. All those objects being interconnected to the cloud, each and every object could be a threat for the whole network. Therefore the security of the objects or the devices is key. Even more, security will become one of the most important assets of the digital world. Contact us to protect your asset and security